The Evolution to Modern Cybersecurity SolutionsThe digital landscape is evolving at an unprecedented pace, bringing with it immense opportunities but also a new generation of sophisticated and persistent cyber threats.
Traditional cybersecurity approaches, often focused on perimeter defense and signature-based detection, are no longer sufficient to protect organizations against advanced
attacks, expanding attack surfaces (due to cloud adoption, remote work, and IoT), and the sheer volume of data.Modern cybersecurity solution products represent a paradigm shift. They are designed to address these contemporary challenges by being more
intelligent, adaptive, integrated, and proactive.

Is an AI- powered external threat intelligence solution that gives security the visibility they need to stay ahead if emerging threats.By unifying Cyber Threat Intelligence (CTI), Digital Risk Protection (DRP), and External Attack surface Management (EASM) into a single platform, LUMINAR enables proactive risk mitigation, real-time insights, and automated threat response. with AI driven intelligence, security teams can anticipate, identity, and neutralize external risk before they escalate streaming operations and strengthening cyber reselience.
Accordion Sample Description Web Intelligence solution equips both expert and novice users with advanced analytics and automated tools to rapidly uncover Actionable Intelligence from all layers of the web. Using AI and big data analytics, Orbis brings users a valuable intelligence quickly and automatically with ORBIS, investigators and analysts can rapidly build suspect profiles, map criminal and terror networks, generate evidence, and detect threats before they unfold.
Connect millions of data points, discover hidden truths, and accelerate decision-makingIn today’s increasingly complex and uncertain environment, analysts and decision-makers require fast answers to complex questions.The growing quantity, diversity, and siloed nature of data makes it challenging to make effective, data-driven decisions.
NEXYTE automatically fuses and analyzes data sources of all formats to provide a rich and cohesive view, and democratizes the power of data science and machine learning to enable users of all levels to reach previously unattainable insights.
NEXYTE empowers organizations to rapidly assess risks, conduct investigations, detect threats, optimize resources and reduce costs across multiple domains, all in one platform.
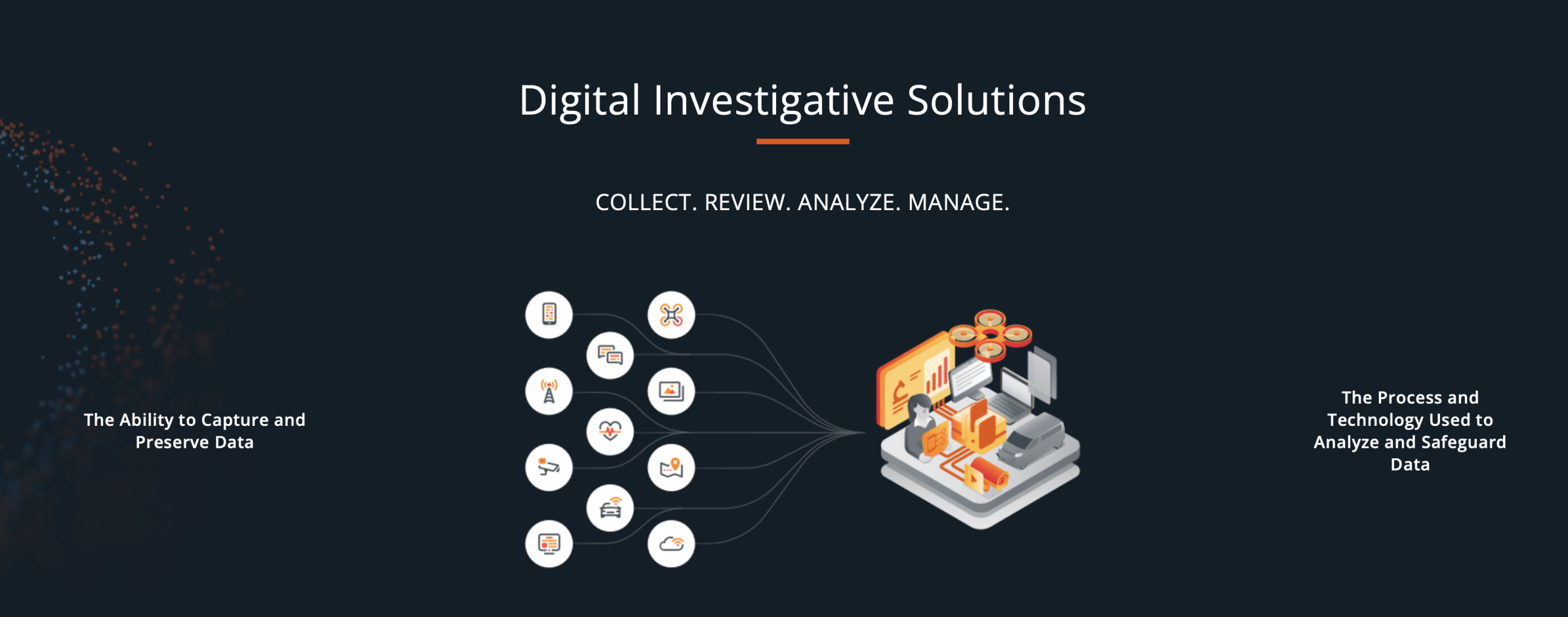
Remotely locate target devices and extract their cellular identifiers
FirstMile is a real-time cloud-based geo-intelligence solution for remotely locating and tracking target handsets over all cellular technologies. The solution enables security agencies around the world to remotely retrieve the location and network identifiers of target handsets in order to analyze their movements and dispatch field units accordingly.
is the world’s first cryptocurrency de-anonymization solution. This groundbreaking, patent-pending technology augments open-source and blockchain analysis with additional sources and techniques. BLINK enables analysts to pinpoint illicit cryptocurrency transactions, follow the money trail, and de-anonymize the identities of transaction makers with no dependency on exchange cooperation.
With BLINK, intelligence and security agencies can reveal the identities of those connected to criminal and terrorist activities to uncover hidden affiliations and business relationships.
Collect valuable active cellular intelligence in challenging scenarios and environments
GI2-S is the leading active cellular intelligence solution for detecting, locating and gaining valuable intelligence from target devices across all cellular networks.
Hundreds of GI2-S units are operated by security organizations around the world, deployed in vehicles or in aircraft, in order to fight terror and crime.
Covertly collect active cellular and Wi-Fi intelligence in complex and inaccessible environments
HIVE is a compact active intelligence solution that overcomes network complexity and radio line-of-sight challenges and provides maximal performance and agility. With its flexible deployment options, HIVE enables field units to covertly collect active cellular and Wi-Fi intelligence under difficult and diverse intelligence gathering scenarios. One HIVE system can fit flexible deployment options including a backpack, helicopter, small vehicle and a motorcycle box.
is a micro-tactical version of GI2, designed for operational missions in which the target’s location is known but its cellular identities are not. HORNET enables field agents to track targets and collect their IMSI/IMEl and additional cellular parameters along with the cellular identities of nearby mobile devices. The target’s cellular identity is then obtained by correlating several snapshots of the collected cellular identities.
Passively intercept satellite communications from wide and distant areas of interest
Si+ is an “all-in-one” tactical off-air solution for simultaneous, passive, and long-range interception of Iridium, Thuraya and Inmarsat mobile satellite communications.
It provides field units with real-time operational agility and offers them a continuous and comprehensive intelligence picture.
is a micro-tactical Wi-Fi and Bluetooth intelligence solution for identity mapping, target intelligence and MiTM access. Due to the ubiquitous nature of Wi-Fi and Bluetooth, investigators often face an intelligence challenge of collecting fragmented data that is transmitted over short distances. The NANO-SNIPER’S pocket-sized dimensions enable close-range intelligence missions that are both covert and versatile. The solution uses a distributed architecture for centralized management and data analysis of multiple deployed sensors.


Meltwater provides media monitoring and social listening tools, leveraging AI to track brand mentions and trends across online platforms.


Specialized in digital forensics, primarily for law enforcement and Enterprise Investigation.